“The Front Lines of Cybersecurity” − Fending Off Hackers and Keeping Our Infrastructure Safe! −
2019/07/31 Toshiba Clip Team

If most of us were pushed to give examples of IoT, we might come up with something vague like network-connected devices or personal tech, without being able to get too specific. Maybe that should be no surprise, because a lot of the advances in IoT are happening behind the scenes, in the industrial sector—in the factory control and manufacturing systems, and in the infrastructure and processes essential for maintaining our way of life. In all of these, digital systems harvest, analyze and visualize data, toward improving operation, output, productivity and profitability.
However, the advances of digital transformation have to be weighed against security. A digitized world is also a more vulnerable world, and that raises a difficult question: how do we keep the industrial sector and essential services safe and secure? What kind of security is needed for infrastructure, and how does it differ from the information security of the past? To get some answers, we talked to Takashi Amano, general manager of Toshiba’s Cyber Security Center.
Security in an age where hackers can take control of social infrastructure
In the industrial sector, IoT has found its way not only into factories, but into social infrastructure like electricity, gas, and water systems. For many of us, that means the threat to our essential services, our electricity, gas, and water systems, is today greater than ever. If malicious hackers were to attack and bring down these systems, they could cause chaos and massive damage, and society would come to a grinding halt.
A wake-up call for many came in 2015, in the Ukraine, when hackers outside the country got malware—a malicious program—into the management system of the country’s electricity grid. They used it and other tools to disrupt the information systems of power distribution companies, take over control of equipment, destroy infrastructure components and data files, and to cause nationwide power outages.
“The Ukraine cyberattack and blackouts were a turning point,” says Amano. “After that, we all felt a sense of crisis about security in the industrial sector. Until then, IoT security was mostly about servers, personal computers and smartphones. But that incident really brought home the understanding that even the critical infrastructure systems we all rely on were now within the realm of the Internet, and could be infiltrated just as easily as a home PC.”

Takashi Amano, General Manager, Cyber Security Center, Toshiba Corporation
This awareness has grown even more prevalent in the past two years, what with cyber attacks on social infrastructure throughout the world. Countries everywhere are mobilizing to protect themselves from these attacks. Now that the digital transformation is sweeping full-speed through the world, the security of the industrial sector is again in question.
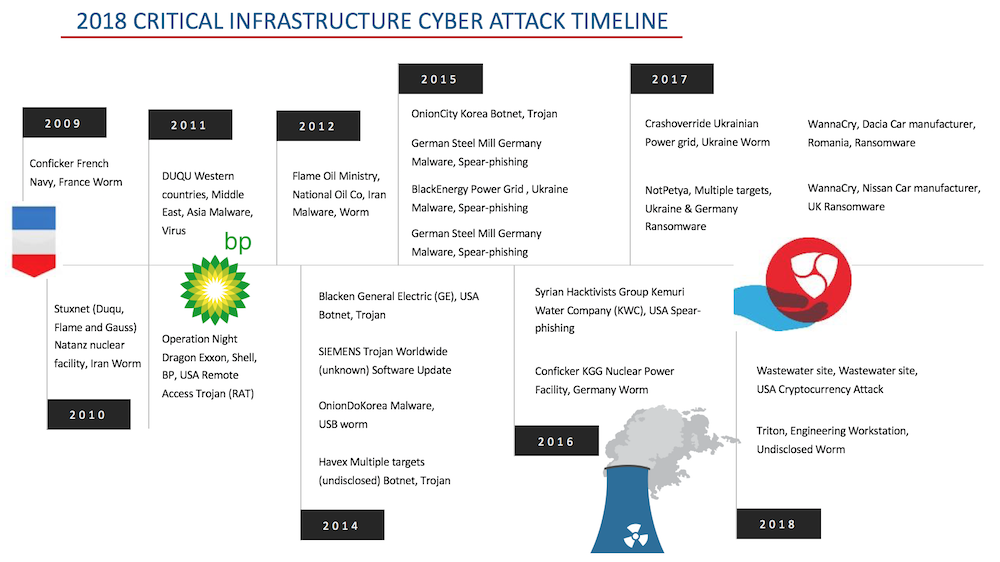
Examples of cyberattacks on vital infrastructure
Toshiba has set its sights on becoming one of the world’s leading cyber-physical systems (CPS) technology companies, able to gather data in the physical world, analyze it in the cyber world, and then return it to the physical world, where it is used to add value to products and services. Recognizing that its own digital transformation involves risk, the company set up an in-house Cyber Security Center in 2017, an organization with the mission of creating a comprehensive information security system for Toshiba Group and for its products and services, dedicated to ensuring security from cyberattacks.
“Until now, information security has centered on three core factors,” explains Amano. “They are referred to as the CIA: confidentiality, integrity and availability. In the industrial sector we also have to consider the three additional factors of HSE: health, safety and the environment, which need to be protected and preserved.” Asked what kind of measures these translate to in the real world, Amano says that answering that question means we first have to think about the motivations of the black hats mounting cyberattacks.
The three axes of IoT security at Toshiba
“Hackers come in all shapes and sizes, from individuals seeing what they can get away with to organizations that work for national governments. In responding, we need to be aware that it is possible to invest too much in security measures, and not only waste money but actually damage the efficiency of work processes and system operation. When creating measures, it’s crucial to first figure out what kind of hacker the system has to deal with, and then take an approach that balances costs with adequate security measures that are always in place.”
We have to recognize that hackers have different motivations. Some cyberattacks are waged to damage reputations, some are denials of service that hit operations, and then there are hacker organizations that are intent on taking over core energy systems.
“In the event of an attack, it’s important to use threat intelligence at an early stage, to figure out who is trying what, and to come up with risk-based countermeasures. In the industrial sector, continuous monitoring and data preservation are important components of data security. That raises two concerns: how do our security systems monitor the constant creation of data, every second and every minute, and how do they preserve that data when there’s a security incident? At Toshiba, our answer to these concerns is a security architecture with three axes.”
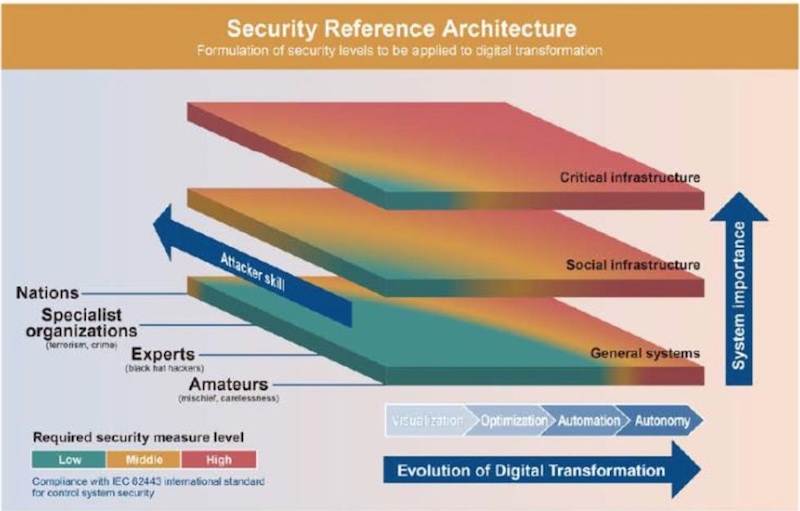
Toshiba’s security reference architecture
The first axis is attacker skill, which can range from amateurs relying on the carelessness of individual users to national-scale cyberattacks.
The second is system importance, which allows Toshiba to define security levels based on the role of the system in question. This extends from individual computers to crucial infrastructure systems, and even to the backbone systems of entire nations.
The third axis is the degree of system evolution.
Amano explains “There are levels to the digital transformation process. It starts with the visualization of data flow, then come updates that make the system more efficient. The next step up is autonomy, through automation and AI. Recently the term “Industrie 4.0” is heard a lot. It originated as a German government initiative to promote the digitization of manufacturing, and basically it’s trying to achieve the autonomous stage of the digital transformation process. Obviously, an industrial site that achieves this level also require high-level security measures and investments as well.”

The idea is to take into account the skills of the attacker and the evolutionary status of the system, and to design security measures suited to that level.
AI + Security = Toshiba doing good for society
It comes as no surprise to hear that AI technologies are at the heart of modern cybersecurity, and also Toshiba’s work in cybersecurity. The company long conducted research and development in AI-related technologies, including audio, imaging and character recognition, and has amassed a wealth of knowledge. However, it’s not just the data analysis skills of human beings and AI systems that are important in these kinds of security measures. Another factor now in the spotlight is the reliability of the “things”—the products, services, etc.—that create the data.
“The systems required for digital transformation are similar in some ways to our Security Architecture,” says Amano. “Both need to be able to analyze, understand, and monitor the data gathered from work sites. Generally speaking, the starting point for security is the reliability of things, and the reliability of the people who use them.
“Toshiba is originally a manufacturing company, and it shows—we’re good at gathering information and data from things and work sites, analyzing and creating simulations with the data in cyberspace using AI and digital technologies, and feeding back the results to the physical world. This is the strength as a company that allows us to prioritize cyber-physical systems (CPS), and we’ll be using it to make further advances in the security field as well.”
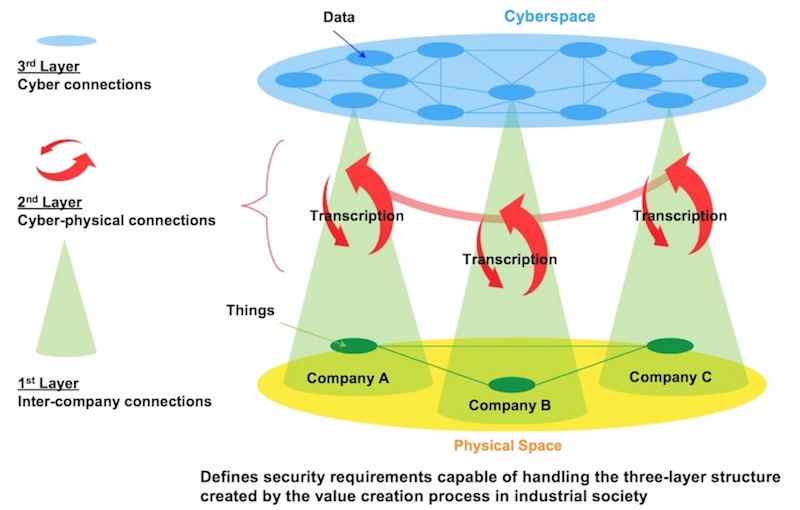
Three-Layer mode of The Cyber/Physical Security Framework (created by Toshiba based on METI documents)
Amano is one of many experts at Toshiba with backgrounds in manufacture, AI and related fields, who are now working on cybersecurity. Drawing on the wealth of resources from developing SATLYS™ analytics AI and RECAIUS™ communications AI, models that use IoT data organically, they are able to give Toshiba an edge in cyber security.
As General Manager of the Cyber Security Center, Amano is responsible for a significant part of Toshiba’s cyber security work. He draws on a rich background in Toshiba’s digital businesses. From research work on antennas, he moved on to projects that included developing tablets and cloud services for TVs. It’s a background that ensures he is well versed in hardware, software, and services, and he is sure that his experience in these different areas has proved valuable in his current work.
“We’ll continue our innovation of security technologies, and our efforts towards cyber security risk management, so as to help create safer and more sustainable societies. On the manufacturing end, we also want to do what we can for a value chain that works well and is safe across all elements, from suppliers to partners, and even customers. To do this, however, we need to make sure the whole value chain has the same level of security. It’s essential that we establish partnerships that consider everything in the value network—the organizations, the people, the things, the data. We have to shift our conceptualization of ourselves as a security vendor, and work to establish partnerships with our competitors, the government, and more.”

![]()