Cyberattacks are a significant threat to critical infrastructure. World-first countermeasure technology rings alarm bells —Part 1
2021/11/08 Toshiba Clip Team
- Worldwide increase in cyberattacks on control systems of critical social infrastructure with potentially catastrophic consequences
- Toshiba and Peraton Labs have developed cyberattack emulation technology
- Unique automated penetration testing system, and collective intelligence of the world

Malware is a growing threat around the world. Cyberattacks can wreak enormous damage on computer systems in critical infrastructure assets such as power plants and substations and transport networks. Cybersecurity is a major priority for Toshiba, which is involved in a range of infrastructure operations. A dedicated team has been assembled at the Cyber Security Technology Division within the Toshiba R&D Center, to bring together expertise from fields such as R&D, operations, technical support and embedded development.
Their latest project is the “Automated Attack Path Planning and Validation (A2P2V)” – also called “cyberattack emulation tool”, a tool that identifies and evaluates vulnerabilities in infrastructure systems by executing cyberattack scenarios in a simulated environment. So how can the world use the emulation tool to deal with the growing menace of cyberattacks? We asked three developers.
Cyberattack is a corporate management issue— a mindset change is needed
“Cyberattacks on control system of social infrastructure are increasing worldwide”, said Hiroyoshi Haruki, the project leader of the cyberattack emulation technology.

Hiroyoshi Haruki
Senior Research Scientist
Security Research Department, Cyber Security Technology Center, Toshiba R&D Center
The cyberattack on Colonial Pipeline, a major American fuel pipeline operator that handles nearly 45% of gasoline and diesel supplies on the east coast, is still fresh in our mind. It wasn’t that long ago that a cyberattack on the Ukrainian power grid caused widespread blackouts. More recently, the rail system in Denmark was targeted in an attack that completely disabled the ticketing system. And the ransomware “WannaCry” was used to inflict damage on public infrastructure assets around the world.
Japan has so far been spared from critical infrastructure cyberattacks. Perhaps because of this good fortune, many Japanese companies tend to associate cybersecurity with level of in-house data breaches, and see it as a negative cost. As Haruki puts it, “despite cybersecurity guidelines in place, few companies give proper consideration to cybersecurity at the senior management level. This is where the investment decisions are made, so they really need to be aware of cybersecurity threats.”

Major infrastructure cyberattacks in recent years
Companies in Japan have often been also slow to recognize the importance of cybersecurity measures. According to a recent report on software vulnerabilities from the Information-Technology Promotion Agency (IPA)*1, there are about 50 security threats occurring every day, which should be addressed as a matter of urgency. Yet according to Haruki, “there are many companies that don’t know how to do with all these threats that require immediate response.”
*1 A semi-governmental organization providing support of technology and human resource for national IT strategies such as information security initiatives and IT skills development programs
The technology was developed to address these very real concerns, by automatically identifying cybersecurity threats and system vulnerabilities with a high degree of precision. That is the cyberattack emulation technology by Toshiba in conjunction with leading U.S. research organization, Peraton Labs. With a long history of innovation dating back to its origins as part of Bell Labs, Peraton Labs develops and delivers leading applied research and high-value solutions across cyber security, communications, machine learning, networking, sensor fusion, and Internet of Things.
Increasingly sophisticated cyberattacks require a system-wide control
Toshiba has been supplying control systems for critical social infrastructure such as steel and petrochemical plants, water supplies and power generation networks since the mid-1970s.Previously, these systems would be tailored to specific industries and sectors, they are increasingly moving towards standardized systems that can be used in multiple settings. One of the key components of the industrial control system is the “Unified Controller nv series™ Type 2”. We can trace a direct line from this component to the cyberattack emulation technology.
The “nv series Type 2” is a major improvement in safe system architecture. Indeed, it is accredited under the “ISASecure® EDSA*2” international standard for control system security. But Haruki and his team wanted to aim higher. As Haruki puts it, “the nv Series Type 2 itself is certainly durable in the face of a cyberattack. But what if the attack targets a different component? Then we’re just as vulnerable. We wanted to create a system-wide security solution.”
*2 ISASecure® EDSA certification guarantees the security of control components based on development phase, implementation of security function and communications durability. ISASecure® is a trademark of ISA Security Compliance Institute.
As it turns out, Haruki wasn’t the only one to see the need for such a solution; at the Toshiba R&D Center, Fukutomo Nakanishi had a similar idea. Together they provided the inspiration for the cyberattack emulation technology.
“Cyberattacks on control systems are increasingly targeting VPNs*3 as a way to get into the system,” explains Nakanishi. “It’s no longer enough to have a secure Toshiba component there; we have to look at the system in its entirety and find the equipment vulnerabilities and path that a malicious actor could exploit. In other words, we have to work out how to construct a secure overall environment.”
*3 “Virtual Private Network” refers to a private secure connection over the internet (or the technology used to create it).

Fukutomo Nakanishi
Research Scientist
Security Research Department, Cyber Security Technology Center, Toshiba R&D Center
Penetration tests are commonly used to identify flaws and vulnerabilities. Experienced engineers known as penetration testers typically execute a simulated attack on a network-connected control system to check for vulnerabilities.
As Nakanishi explains, “it’s a technically complex procedure that requires a high degree of skill. I myself used to be a penetration tester, and I remember that it was really stressful because I was always worrying that I might have forgotten to check some aspect of the system. It seemed to me that the testing process itself is too reliant on the skills and judgement of the individual tester, and I felt that an automated version would be much better.”
Accelerate the world-first technology based on input from ethical hackers and leading security researcher
As Nakanishi points out, the cyberattack emulation technology is essentially a system for generating penetration tests automatically. In more technical terms, it automatically generates attack paths for industrial control systems and executes emulated attacks to verify the strength of system security.
Unlike conventional cybersecurity systems, the cyberattack emulation technology identifies the highest-risk forms of cyberattack as well as key vulnerabilities within the system, which allows the organization to prioritize specific security measures. It has already shown demonstrated benefits using temperature control as a generalized simulation environment.
“In order to understand how the cyberattack emulation technology works, we need to know about penetration testing,” explains Nakanishi. Penetration testing is a four-step process as described below.
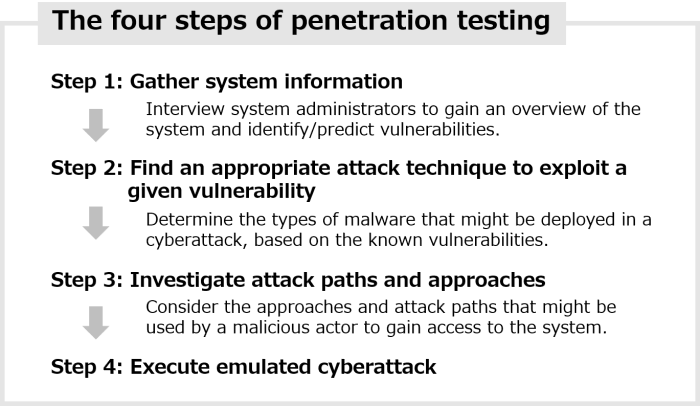
Four steps of penetration testing to verify system security
The first three steps of the process involve planning and preparation, while the last step is the actual attack execution. The entire process involves a great deal of time and effort.
According to Nakanishi, the cyberattack emulation technology comprises a database of cyberattack information, called the attack pattern database, together with the attack path planner and the validator. The database is used for automation of finding an appropriate attack technique to exploit a given vulnerability (step 2), the attack path planner for investigating attack paths and approaches (step 3), and the validator for executing emulated cyberattack (step 4) in penetration testing.
The database represents a massive store of information on known cyberattacks as well as knowledge and expertise of ethical hackers and security analysts inside and outside Toshiba. In combination with the attack path planner algorithms, the database as collective intelligence is used to automatically generate attack paths for the target industrial control system that are then executed by the emulation engine.
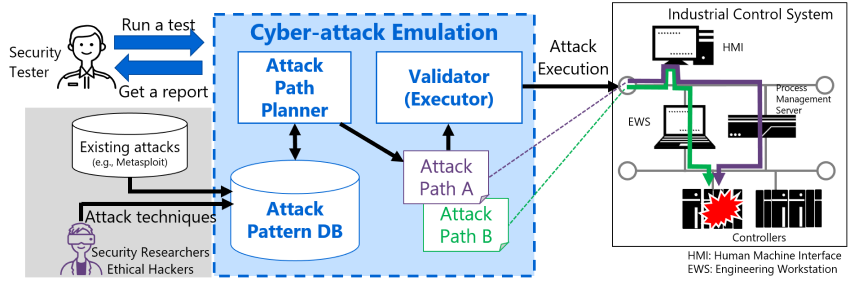
Cyberattack emulation technology automatically generates attack paths and performs simulated attacks
In the next article we will look at the contribution of the Toshiba Group to the development of the Cyberattack emulation technology in conjunction with leading research organization Peraton Labs. We will also explore the concept of open innovation, which involves input from a range of sources including ethical hackers, and consider the future direction of cybersecurity.
![]()
Related Links
*This section contains links to websites operated by companies and organizations other than Toshiba Corporation.
https://www.peratonlabs.com/
Toshiba's Cyber Security | Toshiba