Cyberattacks are a significant threat to critical infrastructure. World-first countermeasure technology rings alarm bells —Part 2
2021/11/12 Toshiba Clip Team
- World-first cybersecurity solution inspired by fight against digital piracy
- Combined expertise of Toshiba and leading cybersecurity research organization Peraton Labs in US
- New Cyberattack emulation technology will help protect social infrastructure

Cyberattack emulation technology from Toshiba and Peraton Labs is designed to identify vulnerabilities in system of social infrastructure such as power plants and substations, water and sewerage systems, transport networks, industrial factories and office buildings, by planning and safely executing simulated cyberattacks.
In Part 1, we looked at the growing threat of cyberattacks on control system of social infrastructure and outlined the history behind the Cyberattack emulation technology, together with a brief overview of how it operates. In Part 2, we will look at why this technology represents such a major breakthrough and examine Toshiba’s specialty in producing this unique solution. We will also consider how collaboration can bring about solving a variety of social issues.
Innovation inspired by knowledge and ideas of the DVD business
“The simulation environment is an important part of the emulation tool. ’Cyberattack emulation technology’ builds a virtual copy of the target control system,” explains Satoshi Aoki, the engineer in charge of developing use cases, identifying required functionality and post testing.

Satoshi Aoki
Security Research Department, Cyber Security Technology Center, Toshiba R&D Center
Cyberattack emulation technology has been validated through trials undertaken in a generalized simulation environment based on a “temperature control system”. The next step is to conduct trials to identify vulnerabilities in various types of public infrastructure such as electricity substations and transport networks, as well as customized industrial control systems in the private sector.
“Toshiba provides products and solutions for social infrastructure in a wide range of industries and sectors,” notes Aoki, “and we work closely with many different business units of Toshiba. This means that we can create extremely accurate simulated environments for the emulation tool. This is the kind of unique expertise that Toshiba can offer.”
But that’s not all Toshiba can offer. Aoki’s colleagues Haruki and Nakanishi both used to work on security measures for computers, TVs and DVDs, including a DVD dubbing protection system designed to limit the number of times DVDs could be copied.
“Our job was to develop solutions to deter hackers from dubbing protections and distribute illegal copies,” recalls Nakanishi. “We designed our security measures from the perspective of an attacker. In the development of Cyberattack emulation technology, the idea of asking ourselves “What would an attacker do?” was one of the basic principles.”

Fukutomo Nakanishi
Research Scientist
Security Research Department, Cyber Security Technology Center, Toshiba R&D Center
Haruki agrees that their experience on DVD security was particularly relevant to the Cyberattack emulation technology.
“We may know a lot about security but we needed to develop on our knowledge on infrastructure control systems,” he explains. “Meanwhile, some members are really well versed in industrial control systems but don’t know much about security. This diversity of experience means that we complement one another to produce a combined pool of expertise. Toshiba has a long and proud history that has generated a substantial knowledge base. The ’Cyberattack emulation technology’ was cultivated based on those technologies and businesses.”
According to Aoki, when fully operational, the emulation tool will allow anyone to generate security evaluation testing to a consistently high standard without the need for specialized expertise. “It will significantly reduce the project lead time and expense, because there’s no longer any need to bring in an external researcher or expert. A dedicated penetration tester would only be required in the event that a more in-depth investigation was deemed necessary.”
Open innovation has realized accurate development in a short period of time
Cyberattack emulation technology makes full use of Toshiba’s key expertise. Haruki describes it as “a project of enormous significance for wider society.” A key underlying principle of the project is that security solutions for critical infrastructure should be made widely available, not limited to Toshiba Group products and industrial control systems. More importantly, key elements of this project were a joint initiative and open source.
The joint development of cyberattack emulation technology drew on the expertise of Peraton Labs, a leading research organization across cyber security, communications, machine learning, networking, sensor fusion, and Internet of Things based in the United States. Nakanishi describes how the two organizations came to work together.

Peraton Labs has a storied history of innovation dating back to the world-renowned research institute, Bell Laboratories
“Cyberattacks are becoming increasingly complex and sophisticated, and it is vital that cybersecurity research keeps up,” notes Nakanishi. “But it requires a significant investment of time, so we started to explore our existing partnerships with universities and research institutes. Eventually were thrilled to be able to team up with Peraton Labs, which boasts considerable experience and expertise with penetration testing and cybersecurity.”
“Peraton Labs and Toshiba have a strong history of teaming on joint research and development of innovative tools and solutions for critical infrastructure protection as well as contributions to open standards,” said Subir Das, Chief Research Scientist, Peraton Labs, standing at far left in the A2V2P team photo. “To achieve the automation goals in this project, we leveraged our expertise in vulnerability analysis, advanced analytics, machine learning, and cyberattack construction and defense, in close collaboration with Toshiba.”
Peraton Labs developed the inference and emulation engines—the algorithms used to identify attack paths into a system and execute a simulated attack—while Toshiba was responsible for creating the simulated environment of an industrial control system. The two partners worked closely together in constructing the Attack Pattern Database based on mutual discussion and knowledge about cyberattacks. In a relatively short space of time, the technology was ready to present to the international security conference Black Hat USA 2021 Arsenal.
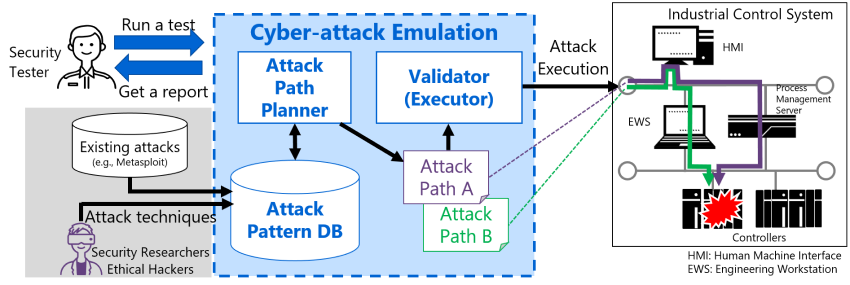
The Cyberattack emulation technology performs simulated attacks based on automatically generated paths
Haruki emphasizes the importance of setting up a joint research framework that draws upon the respective strengths of both partners. “The Toshiba group as a whole is strongly committed to open innovation as a way to generate new forms of value through co-creation.” Open source can be seen as a natural extension of this principle.
Open source refers to the practice of releasing source code into the public domain at no cost. The source code for the Cyberattack emulation technology is freely available on GitHub. Aoki explains the motivation thus: “We wanted to promote Toshiba’s commitment to cybersecurity as widely as possible. And we wanted to enrich connections with security technology across the whole social spectrum, while at the same time further refining the technology.” The project represents a coming together of like-minded people united in their mission to create technical solutions to help make the world safe and secure. Striving for self-sufficiency is a major barrier to innovation. The Cyberattack emulation technology is representative of Toshiba’s commitment to open innovation.

Hiroyoshi Haruki
Senior Research Scientist
Security Research Department, Cyber Security Technology Center, Toshiba R&D Center
Taking offense and defense to the next level—Toshiba expertise and philosophy
You may think that the development process all went smoothly, based on what’s been described above. But in truth, there were many challenges and obstacles along the way—after all, it was a world-first technology.
At present, simulated penetration tests on industrial control systems are generally based on the BAS (breach and attack simulation) approach. This is the same as the concept that underpins the Cyberattack emulation technology, although as Nakanishi points out, “Because BAS testing uses an abstraction of an infrastructure control system, it can detect the possibility of that control systems which are highly likely to contain vulnerabilities.” In other words, there is still room for improvement with respect to precision.
The intention is for the Cyberattack emulation technology to deliver the same level of precision as conventional penetration testing performed by a specialist engineer. To this end, the emulation tool features a database of attack patterns that combines known attack strategies and methodologies with the expertise of security analysts. This information is then used to automatically generate and execute cyberattack scenarios (attack paths) for industrial control systems. According to Nakanishi, this was the most challenging aspect of the development process, involving a great deal of trial and error in compiling the database, generating attack paths and applying them to the simulated environment of an infrastructure control system. Precision levels gradually improved through successive iterations.
Some readers may have noticed an important distinction in nomenclature: Toshiba has chosen the term “emulation” instead of “simulation” as in the BAS (breach and attack simulation) approach. The choice of emulation over simulation reflects that the emulation tool generates attacks that are executed in a simulated operating environment that represents a highly realistic rendering of a system
Creating the Cyberattack emulation technology presented many challenges, not least the amount of time and effort needed to reach the required level of precision. The emulation tool identifies the paths that could be employed by different attack strategies to gain access to infrastructure control systems—in other words, it illustrates specific vulnerabilities and paths that could be used by a malicious actor to mount an attack. As the old adage says, “If you know yourself and your enemy, you need not fear one hundred battles.” And as Nakanishi noted, the emulation tool really takes this technology to the next level.
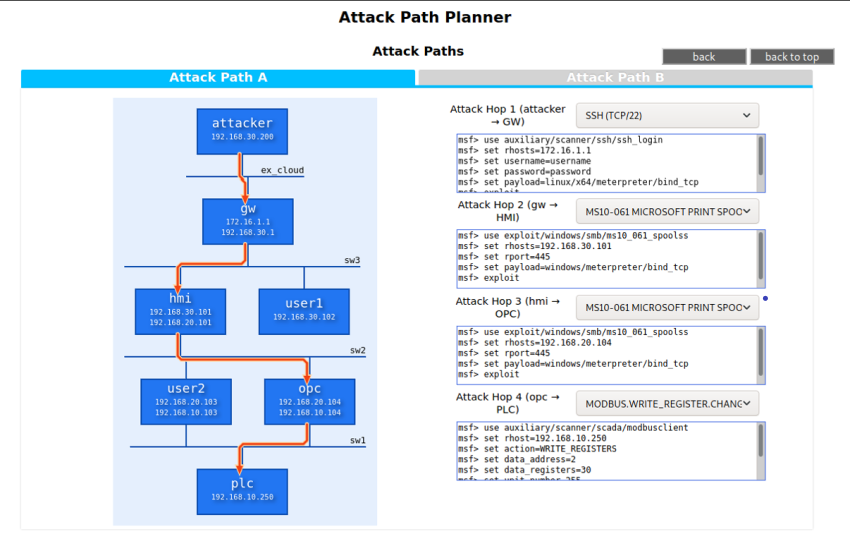
User interface of Cyberattack emulation tool
“Around 50 security threats are reported every day,” says Nakanishi. “Often these are described only in terms of vulnerabilities, and we do not know the attack strategy that was used. Now, it’s simply not viable to treat vulnerabilities where the attack methodology is known as equivalent to with those where the attack methodology is unknown. What we need to do is to prioritize vulnerabilities that we know can actually be exploited. And this is precisely what the Cyberattack emulation technology is designed to do.”
In order to stay ahead of malicious actors, we must be always looking to identify weak points in the system and take action before attackers have a chance to exploit them. Haruki is confident that the Cyberattack emulation technology will allow organizations to achieve this without the need for specialized skills. “Although we are still trialing it in a simulated environment at the moment, in the future we expect it will deliver significant benefits not just for Toshiba group products and solutions, but with respect to the full range of public infrastructure systems.”
Our sense of duty is driven by the Essence of Toshiba, which serves as the core foundation for sustainable growth and for all aspects of our operations. Part of this is the Our Purpose statement, which calls for:
A planet that’s safer and cleaner.
A society that’s both sustainable and dynamic.
A life as comfortable as it is exciting.
“Our Purpose talks about safety—that’s our social responsibility,” says Haruki. “We are strongly committed to keeping society by providing cutting-edge security solutions.”
![]()
Related Links
*This section contains links to websites operated by companies and organizations other than Toshiba Corporation.
https://www.peratonlabs.com/
A2P2V · GitHub
Toshiba's Cyber Security | Toshiba